Turn Assumptions into Trust
Use trackable seed contacts for vetting data partners and data leak monitoring.
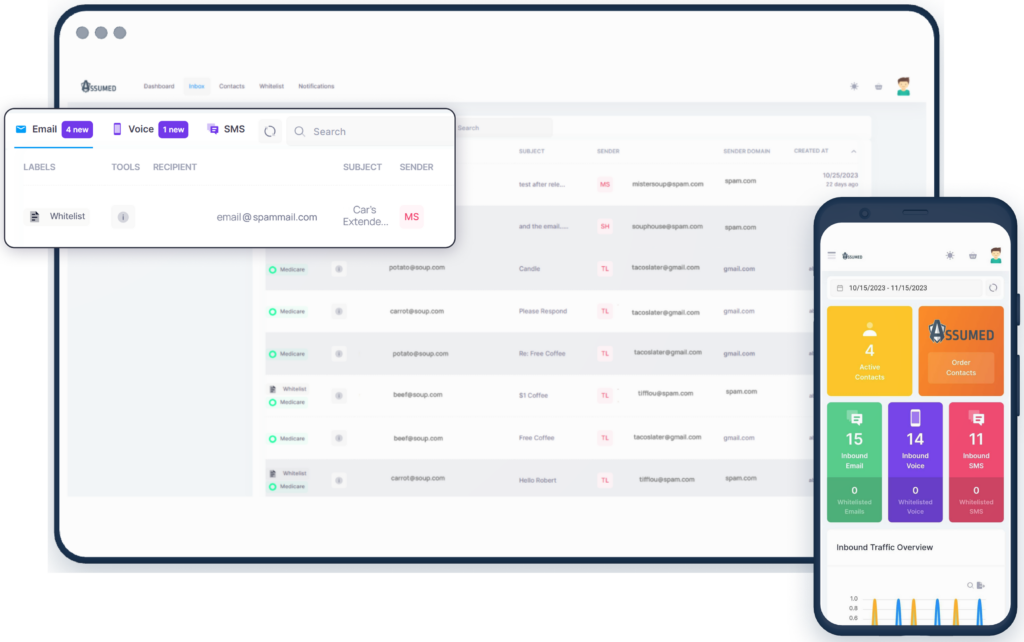
Assumed Solutions
Don’t let security concerns hold your business back, give yourself peace of mind with our different security solutions.
Detect Indicators of Data Leaks
Use Assumed Seeds as honey tokens in your database or lists to find out if they have been compromised.
Vet Your Data Partners
Your customers should not have a bad experience, find out what communications they are receiving and by who.


Validate Customer Experience
Dozens of phone calls and texts in a day is unacceptable. Prove that partners are doing what they should be with data.
Never Miss A Beat
Stay current with all the latest product launches, industry trends, and security news to ensure your business consistently stays secure.




Latest News
-

5 Ways Managed Security Service Providers or Consultants Can Use Assumed Seeds to Better Serve and Keep Their Clients
Hey there, cybersecurity pros! Are you an MSSP looking to……
-

Automate Your CRM Seeding Process
Is monitoring your CRM or lists too manual or cumbersome?……
-

How to Use Assumed Seeds for Market Research
Assumed Seeds are artificial consumer contact records with real working……
-

Stop Guessing, Start Coaching: How Assumed can Elevate Client Recommendations
As a sales coach, you know that having insight into……
-

Is it Safe to Assume That…?
Is it Safe to Assume That…? A common phrase often……
-

Your Business is Your Castle – Build it Like One.
In an age long ago, medieval architects were tasked with……
