December Update: Assumed Exports Expansion
At Assumed, we’re constantly listening to how you use your seed contacts to protect your data. Whether you’re vetting a ...
Read MoreAt Assumed, we’re constantly listening to how you use your seed contacts to protect your data. Whether you’re vetting a ...
Read More
As we gather to celebrate the holidays—a season of gratitude, reflection, and connection—we at Assumed extend our heartfelt wishes to ...
Read More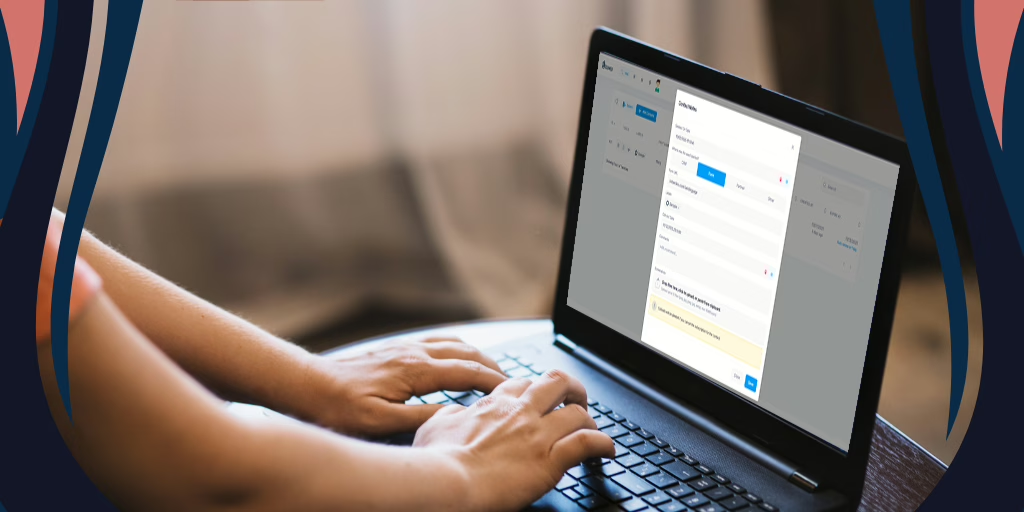
We’re excited to announce a new feature that will simplify and organize contact management for Assumed Seeds: Contact Notes. The ...
Read More
Even if you initially track how vendors use consumer data, does this sound familiar? A mid-sized insurance lead buyer noticed ...
Read MoreOctober isn’t just about falling leaves and pumpkin spice; it’s also Cybersecurity Awareness Month 2025, an initiative that Assumed is ...
Read More
As a small business owner, you might wonder, “Do I need cyber insurance, or is my operation too small to ...
Read More
The lead generation industry took a hit to its reputation, but this is not the first time. The Bene Market ...
Read More
Small and medium-sized businesses face many cybersecurity challenges as they grow, so getting cyber insurance 2025 is important. While implementing ...
Read More
On May 9, 2024, Maryland joined the growing list of states with comprehensive data privacy laws by enacting the Maryland ...
Read More
What is Data Loss Prevention Software? Data loss prevention software refers to specialized security tools that detect and prevent unauthorized ...
Read More
Our mission is to assist companies in their fight against data leaks. We strive to provide a data leak monitoring and data partner vetting solution, giving businesses the tools and knowledge they need to monitor their most valuable asset: their data.
Assumed LLC
1731 N Marcey St., Suite 525
Chicago, IL, 60614