What is NIST cybersecurity framework 2.0?
NIST, the National Institute for Standards and Technology, recently released a significant update to its popular Cybersecurity Framework—NIST CSF 2.0. The CSF was created in 2014, and the NIST Cybersecurity Framework 2.0 is its first significant update in almost six years.
Table of Contents
The NIST CSF is an easy-to-use framework used by companies of all shapes and sizes committed to reducing cybersecurity risk. We like the CSF because it serves as a simple guide for creating security controls that can help protect your business and customers from cyber threats. In fact, at Assumed, we use the NIST CSF to build the foundation of our information security program. It’s a great starting point and can lead you to the best practices you must implement for a solid information security program.
The NIST CSF, however, is not all you will need. Think of it as a “getting started guide.” This is because the CSF is descriptive rather than prescriptive. In other words, it can provide helpful guidance, but you must still develop and implement the controls that best meet your security needs.
What’s the new cybersecurity framework?
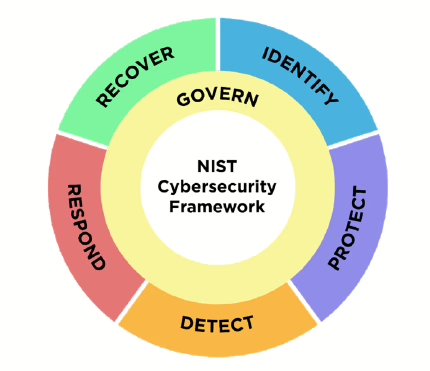
So, what’s new with CSF 2.0? The Cybersecurity Framework includes over 100 sub-categories organized into the following functions: identify, protect, detect, respond and recover. The 2.0 update adds a new function called GOVERN. This makes sense because governance is important in a successful information security program. The govern category borrows some control guidance previously found in the other categories and introduces new concepts. There is an increased emphasis on risk management, ongoing monitoring and supply chain management (think 3rd party risk).
While the NIST CSF is intended to be accessible and applicable to all businesses, much work is required to make it a practical part of your information security strategy. This ranges from policies and procedures to technical controls and often involves implementing third-party tools and services needed to help you reach favorable outcomes. A single tool certainly can only do some of it, but Assumed Seeds fits quite well with a number of the NIST guidelines, which means that you don’t have to build or deploy expensive, complex solutions to meet the requirements in several areas of focus. Here are some examples of what Assumed can do in the context of your cybersecurity framework.
How Assumed can help
| NIST CSF 2.0 Control Guidance | How Assumed DLM Can Help |
| GV.SC-06: Planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships. | Are you planning on contracting with a new data supplier? Use Assumed DLM to conduct due diligence and vet potential partners. |
| GV.SC-07: The risks posed by a supplier, their products and services, and other third parties are understood, recorded, prioritized, assessed, responded to, and monitored over the course of the relationship. | Use Assumed DLM to validate a supplier’s data handling practices and monitor them throughout the relationship. |
| GV.SC-09: Supply chain security practices are integrated into cybersecurity and enterprise risk management programs and their performance is monitored throughout the technology product and service life cycle. | Assumed DLM can continuously monitor incoming communications and provide you with indicators and alerts of undesirable behaviors. |
| ID.RA-10: Critical suppliers are assessed prior to acquisition. | Assess your data suppliers by vetting their practices before entering a data exchange partnership. |
| DE.CM-01: Networks and network services are monitored to find potentially adverse events. | Use Assumed DLM to monitor internal systems and databases where you store sensitive contact information. |
| DE.CM-06: External service provider activities and services are monitored to find potentially adverse events. | Place Assumed seed records in external contact databases/CRMs to monitor the security of external services. |
If you want to dive deeper into NIST CSF, you can drink right from the source at: https://www.nist.gov/cyberframework.
You can learn more about Assumed on our website or by contacting us to discuss how Assumed can support your security and compliance journey with simple but effective solutions to detect data leaks, monitor contact databases, and vet your data suppliers.

