Businesses must recognize the importance of vetting their vendors in the vast and intricate world of data sharing. A recent case study we conducted at Assumed is a stark reminder and begs the question, “How are you vetting a new vendor?”.
The experiment
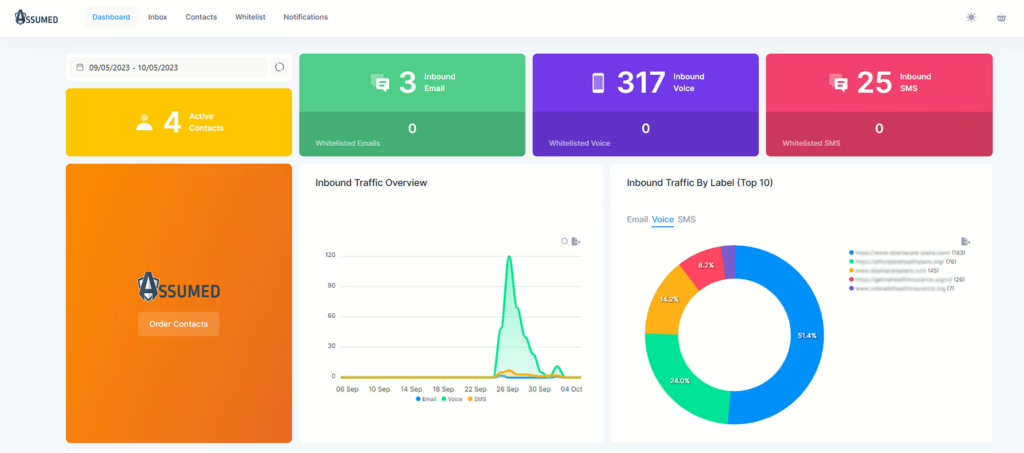
We embarked on a small experiment to understand the magnitude of data sharing in the health insurance sector. Our team filled out a health insurance form using one of Assumed’s decoy contact details. The results were astonishing and alarming in equal measure.
Within just 2 days, the Assumed contact received over 300 phone calls. This staggering number raises a crucial question: Why is this one contact receiving this many calls in just hours after submitting a form? Did the consumer filling out the form know what they were engaging in? Would they have still submitted the form if they knew they would get so many calls? And of course, do you want to deal with leads that have to endure that experience?
The implications
The immediate reaction of this experiment is apparent: data entered into a health insurance form is often sold to many partners. In some cases, these companies have no idea what the user experience is. In other cases, they just don’t care how often the consumer is contacted. This can lead to a barrage of unsolicited calls, messages, and emails, causing significant inconvenience and a poor user experience. Such leads will end up costing companies more in the long term through wasted time, low quoting/closing rates, and the need to increase communication frequency to try and recoup the campaign costs.
The importance of vetting vendors
This experiment shows the critical importance of vetting vendors. When businesses share data with vendors without a thorough vetting process:
- Data Misuse: There’s a risk that the data might be misused or re-sold to third parties.
- Reputation Damage: Businesses might suffer reputational damage if customers feel their data is not handled responsibly by the company that generated it.
- Potential Legal Repercussions: In many jurisdictions, sharing data without consent or due diligence can lead to legal penalties.
- Poor Performance: Companies often see high CPAs and complaints when dealing with poor quality vendors.
How are you vetting a new vendor? Assumed can help.
Assumed’s data leak monitoring offers a robust solution to this challenge. By using decoy contacts, Assumed can help businesses identify vendors who might be sharing data irresponsibly. Here’s how it works:
- Decoy Contacts: Assumed creates decoy contact details that are embedded within your real data.
- Monitoring: From the Assumed dashboard, you can monitor unsolicited communication and measure how often and by whom these contacts are being contacted.
- Identification: The data is being re-sold, or the vendors are not being responsible with the data if the decoy contacts receive irrelevant or excessive communication.
- Action: Businesses can then act appropriately against the vendors accountable for the misuse.
Conclusion
In an era where data is often termed the ‘new oil,’ responsible handling is crucial. Our experiment with the health insurance form highlights the pitfalls of unchecked data sharing. By vetting vendors rigorously and employing tools like Assumed’s data leak monitoring, businesses can ensure that their data, and by extension their reputation and legal standing, remains secure.

